Authentication is knowing the identity of the user. For example, Alice logs in with her username and password, and the server uses the password to authenticate Alice.
Authorization is deciding whether a user is allowed to perform an action. For example, Alice has permission to get a resource but not create a resource.

Basic Authentication
Basic authentication transmits credentials as user ID/password pairs, encoded using base64. The client sends HTTP requests with the Authorization header that contains the word Basic word followed by a space and a base64-encoded string username:password.
1
Authorization: Basic ZGVtbzpwQDU1dzByZA==
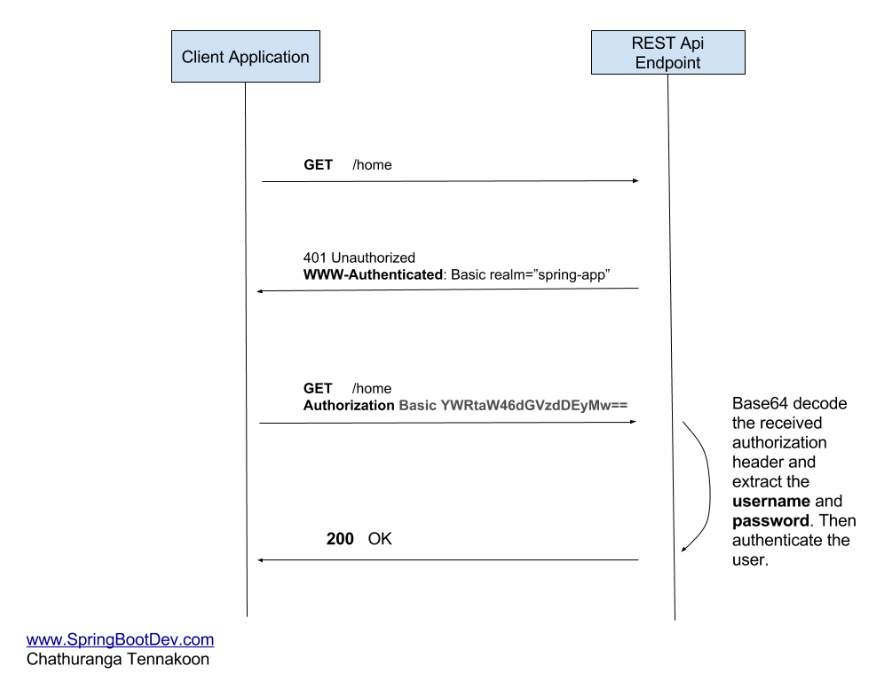
For basic authentication, as the user ID and password are passed over the network as clear text (it is base64 encoded, but base64 is a reversible encoding), the basic authentication scheme is not secure. HTTPS / TLS should be used in conjunction with basic authentication.
Digest Authentication
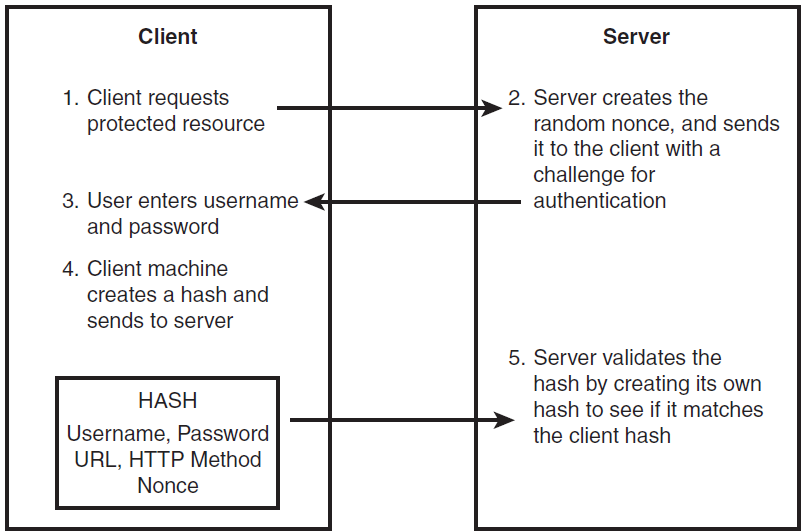
- Client makes request
- Client gets back a nonce from the server and a 401 authentication request
- Client sends back the following response array (username, realm, generate_md5_key(nonce, username, realm, URI, password_given_by_user_to_browser)) (yea, that’s very simplified)
- The server takes username and realm (plus it knows the URI the client is requesting) and it looks up the password for that username. Then it goes and does its own version of generate_md5_key(nonce, username, realm, URI, password_I_have_for_this_user_in_my_db)
- It compares the output of generate_md5() that it got with the one the client sent, if they match the client sent the correct password. If they don’t match the password sent was wrong.
典型的认证过程包括如下步骤。
客户端请求一个需要认证的页面,但是不提供用户名和密码。通常这是由于用户简单的输入了一个地址或者在页面中点击了某个超链接。
服务器返回401 “Unauthorized” 响应代码,并提供认证域(realm),以及一个随机生成的、只使用一次的数值,称为密码随机数 nonce。
此时,浏览器会向用户提示认证域(realm)(通常是所访问的计算机或系统的描述),并且提示用户名和密码。用户此时可以选择取消。
一旦提供了用户名和密码,客户端会重新发送同样的请求,但是添加了一个认证头包括了响应代码。
在这个例子中,服务器接受了认证并且返回了请求页面。如果用户名非法和/或密码不正确,服务器将返回”401”响应代码,然后客户端会再次提示用户输入用户名及密码。
Bearer Authentication
Bearer authentication (also called token authentication) has security tokens called bearer tokens. The name “Bearer authentication” can be understood as “give access to the bearer of this token.” The bearer token is a cryptic string, usually generated by the server in response to a login request. The client must send this token in the Authorization header when making requests to protected resources:
1
Authorization: Bearer < token >
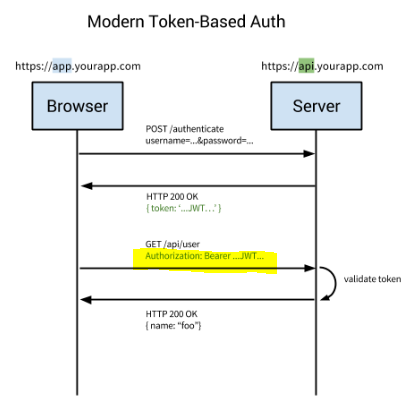
Note: Similarly to Basic authentication, Bearer authentication should only be used over HTTPS (SSL).
The Basic and Digest authentication schemes are dedicated to the authentication using a username and a secret (see RFC7616 and RFC7617).
The Bearer authentication scheme is dedicated to the authentication using a token and is described by the RFC6750. Even if this scheme comes from an OAuth2 specification, you can still use it in any other context where tokens are exchange between a client and a server.
Basic Authentication
Bearer Authentication
https://stackoverflow.com/a/34022350/7352168
https://stackoverflow.com/questions/8483717/digest-basic-and-bearer-authentication
开发者必备知识 - HTTP认证(HTTP Authentication)
Basic and Digest mixed authentication with WebAPI
DotNetDigestAuth
Most Used REST API Authentication Methods
What is digest authentication?
Authentication schemes
Hypertext Transfer Protocol (HTTP) Authentication Scheme Registry